IT security – at the heart of a completely secure IT infrastructure

“We are proud that we protect Audi.
Helge Arndt, Threat Intelligence Analyst
Security with a system
Audi’s entire process chain has to deal fundamentally with the issue of IT security. From basic questions of data protection and threat detection through to attacks such as ransomware attacks and ‘phishing’ – the number of potential threats to company networks and IT infrastructures is constantly increasing. These may be in production or in the office, but also in the various vehicle services. We counter these dangers with a strong IT security organization. We work in networked product teams which are in close contact with each other. Together, they ensure that Audi’s whole IT system landscape, as well as its business and production processes, are protected from attacks by hackers and that current threats are assessed.
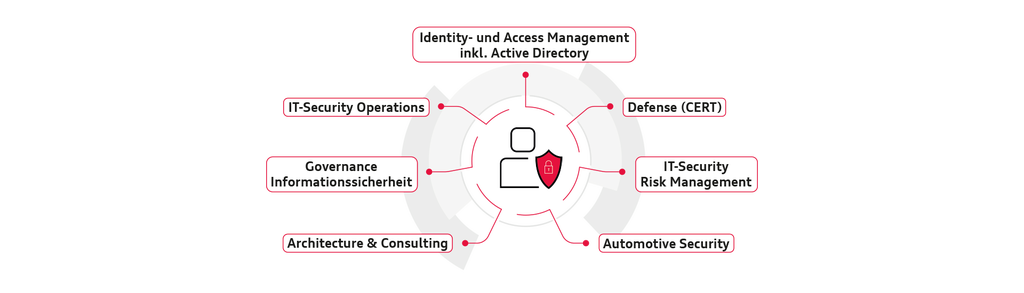
The product teams contribute in different ways to this task of providing first-class information security. We enable the secure use of cloud applications, provide a future-proof Active Directory for the whole group, support the Audi departments in the security-compliant implementation of IT solutions and protect the entire IT infrastructure from attacks. Issues such as IIoT (the industrial Internet of things), cloud computing, big data and smart factory are all in a day’s work. We use hybrid-agile methodology and are ready every day to react to new developments.

“Something new every day.“
The Defense Team, also known as the Computer Emergency Response Team (CERT), has an overarching role in information security. Here we trace potential vulnerabilities with investigative skill, assess cyber-attacks and repel them. However, we do this not only in close coordination with all the IT security product teams within Audi, but also by communicating with product teams in the entire VW Group. In this way we support each other, so that we’re ready again every day to be one step ahead of the threats in the cyber world.
“In my CERT team, I look every day at what is currently going on in the entire IT security world. I detect new trends or potential security gaps. The aim is to identify possible threats, such as supply chain attacks and ransomware, and to do something about them at an early stage. I learn something new every day. That’s just part of it.”
Helge Arndt, Threat Intelligence Analyst

More details
3 questions to a threat intelligence analyst
What does a typical working day look like in your team?
First and foremost, I analyze the overall threat situation for Audi – internally and externally. To do so, I find information in various Internet forums and in the digital media about existing or possible threats to Audi. Through conversations with other IT experts or hackers, I track current trends at the same time. Or I analyze security incidents at other car manufacturers or companies and in what way these could also become relevant to Audi.
What would you look for in a new colleague to work in your area?
Let’s put it this way, the ideal candidate doesn’t exist. We’re a team who work closely together and in which everyone must be able to rely 100% on each other – especially in crisis situations. We all complement each other, which is why each individual should bring as many different facets, functions and expertise as possible to the team. For this you also have to have the necessary willingness and ability to learn so you can develop further. Always be on an equal footing with the technical developments: where are they going? What can I improve? What new things can I discover or what can I develop or script myself in order to identify new issues and be able to react to them?
So, you shouldn’t focus single-mindedly on one area, but must ultimately always be able to look around and spot what is going on elsewhere. The most important people for this are team players who function optimally in cooperation with others. It’s no use if individuals only look to themselves and pursue their own line, that doesn’t work in a team. Because in a team we represent each other, and each individual’s expertise is somehow made available to the whole team so that we can successfully do our work.
What are the greatest challenges for IT security now or in the future?
There is currently a strong trend towards supply-chain attacks and ransomware attacks, including way beyond the car industry. Here attackers gain unauthorized access via partner companies and suppliers in order to reach their real target. This is a relatively easy gateway into big companies and a lucrative target for the hackers – it’s known as ‘big-game hunting’. In Audi’s environment, too, security incidents have more than doubled in the last few years.
But, of course, the issue of home working is also becoming exponentially more important. Employees are no longer fully in the company. Despite the VPN tunnel, this constitutes another point of attack for companies as well as for us.
Another issue is the area of cloud technology, where Audi is more or less dependent on third parties and their infrastructure and security solutions.
“We create security together.”
“Every day as a team we try to understand what the current threats are. We can only do this together because the cyber world is so incredibly diverse and fast-moving, which is why we need all perspectives. The worst thing in Defense is if everyone has the same view. My central task as team lead is then to initiate internal discussions, to build bridges and to bring experts on board in a targeted way.”
Mona Lang, Product Team Lead IT Security Defense

More details
3 Fragen an eine Product Team Lead
What does a typical working day look like in your team?
In our area you never really know what is coming your way. Obviously, we have clearly regulated processes which structure security incident management, but agile and dynamic cooperation in our product teams is just as important. Here we define individual strategies and then work on specific core issues. We’re also a product team and have a wide range of focus areas, whether it be to better monitor and protect technologies, systems or products (e.g., Office 365). And, of course, there is still the familiar ticketing system which is basically used to manage our IT processes.
What would you look for in a new colleague to work in your area?
Character traits are the most important, because you can learn almost everything else if you want to. But the appropriate curiosity and the desire to learn something new, that’s particularly part of someone’s personality. Team players definitely find it easier here. You must be able to take on and understand other points of view in order to then look for a solution together. That’s why our team is also set up to be professionally diverse. Ideally, we try to have colleagues with different levels of experience on board so we can address problems around the issue of cyber security from different perspectives.
Our experts must always stay up to date, too. Above all, this requires the motivation to continually find out about the widest range of issues, trends and developments. On the one hand, we achieve this by regular training courses to further develop our professional and technological knowledge in line with existing knowledge and, on the other, through intensive information exchange with other departments. After all, security incident management doesn’t end at Audi’s corporate borders, we also look at the other brands and the VW Group. That’s why speaking English is part of our working life and it never hurts to be able to speak other foreign languages in the field of threat intelligence.
What are the greatest challenges for IT security now or in the future?
Besides ransomware and supply-chain attacks, it’s the two issues of security in industrial plants and automated IT security. In future, external cyber-attacks will be carried out increasingly rarely by real people. Consequently, this also eliminates the usual human breaks in which, up to now, we’ve been able to react to criminal attacks. The only solution to this will be the development of in-house security solutions which will be able to analyze and combat security incidents in a fully automated way as well. As to the issue of security in industrial plants, we are observing a development throughout the industry towards more ransomware attacks to, for example, cripple production. Through discussions with the relevant department, we try to identify where there is important potential to improve monitoring. This enables us to detect future attacks more quickly and respond to them with the right technology.


